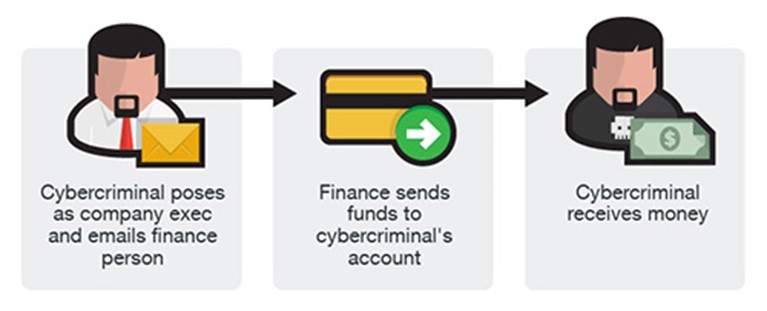
Business email compromise (BEC) scams are online payment fraud that targets businesses and can result in significant financial loss. BEC involves gaining unauthorized access to a legitimate email, text message, or social media account, or an attempt to spoof or fake a legitimate account.
The purpose is to enable the criminal to send a message from an executive or business leader, vendor, or client to convince an employee to transfer funds.
Once these funds are transferred to the criminal actor, it’s difficult, if not impossible, to recover the loss. Between 2016 and 2021, Americans lost approximately $9 billion to BEC fraud. It takes only minutes for a financially crippling mistake – and it can happen to anyone. Whether it’s a new hire, a 20-year veteran, a payables manager, or a CEO, the resulting impact is the same.
The good news is there are actions businesses can take to minimize and mitigate their risk.
How to identify BEC red flags and reduce risk
The most important preventative measures against BEC are vigilance and awareness. Below are several BEC red flags to look for when you receive communications regarding funds transfers or transactions.
Communication features
- Spoofed communications – Thoroughly inspect spelling and domains on payment requests received via email. Carefully check the address of the sender (email, phone number, etc.) to see if letters, numbers, or the domain name are incorrect.
- Use of personal accounts – Criminal actors will impersonate company leaders, vendors, or clients who are using their personal accounts (email, mobile phone, social media) rather than their standard company accounts.
Focus on timing
- Urgency – Criminal actors using BEC write communications requesting quick action on data changes or funds transfers, or they set accelerated deadlines. The faster timelines can result in missed validation steps or the employee acting outside of the protocol.
- Relying on employees’ response to authority – These actors depend on employees being conditioned to quickly comply with requests from executive leadership or important clients and vendors.
- The request comes at a busy time – Many fraudulent requests will come at the end of the workday or workweek, putting pressure on employees to complete the request before the end of business (or end of month/quarter/fiscal year).
Communication and behavior
- Communications from executives – BEC fraudsters will impersonate a real individual, most often a leader or executive at the company a person works for.
- Single form of communication – Many BEC attempts will indicate the sender is in a meeting or traveling and can’t be reached by phone or other means, and demand all communication occurs via a specific communication channel such as email, text, or social media.
- Generic terms and odd grammar – Emails with non-personalized greetings such as “Dear”, “Sir” or “Customer” are red flags. Emails with odd grammar, such as “kindly,” missing punctuation, or spelling errors, are also red flags.
- Combined with fear and urgency, the prospect of being rewarded may prompt employees to skip typical procedures. These rewards can be tangible or intangible, such as being recognized for solving a problem or completing a highly important task for executive leadership.
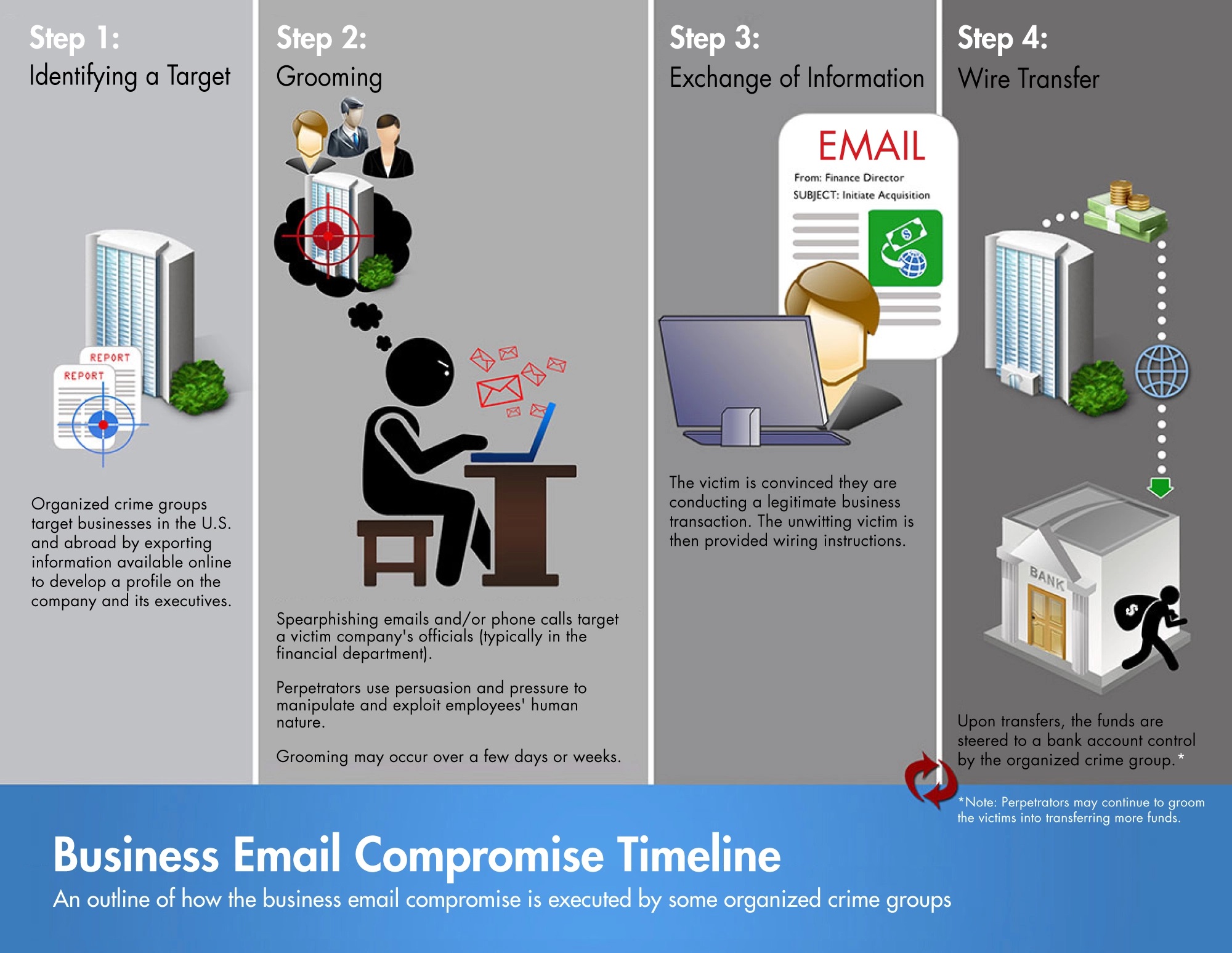
How a company is targeted for BEC
Before launching a BEC scam, criminal actors may research the company, employees, and senior management to gather as much information as possible to help them craft a convincing request. They may even check travel schedules, read other business emails, and review social media profiles.
Criminal actors most often identify themselves as a high-level executive (CFO, CEO, CTO, etc.), lawyer, vendor, customer, or other representative. In the communication, they will claim to be handling confidential or time-sensitive matters and request the initiation of an urgent wire transfer.
Notably, these urgent requests also include a change to the receiving account or setting up a new account (which ultimately routes to the criminal actor). The employee may believe the request is legitimate and execute the fund’s transfer.
BEC is a social engineering scam
The tricky part about BEC is it isn’t primarily achieved through malware or hacking – it uses social engineering. These criminal actors create believable scenarios that can trick an employee into transferring funds.
Social engineering uses deception to manipulate individuals into divulging confidential information or taking action to support fraudulent activity.
It is in our nature to trust and want to help. Cybercriminals use psychology and human nature to entice victims to bypass important security controls.
How to help prevent BEC
Thoroughly vet payment change requests.
A request for payment accompanied by a change in receiving account should always be closely examined.
Contact executives, vendors, or clients using an alternate communication channel to verify the request and the new account information. Ensure contact is made using a trusted phone number for a known contact at the organization, not the phone number provided in the email, text, or social media message, and verify the individual is authorized to make the request.
Pause to verify.
When asked to verify a wire transfer, delay the transaction until additional verifications can be performed, and require dual approval for any wire transfer request that meets certain high-risk criteria.
Keep it simple.
Limit the number of employees authorized to approve and/or conduct wire transfers.
Create an environment of trust.
Many BEC scams are a result of criminal actors posing as senior leaders within organizations. Employees should feel comfortable pausing to validate a senior leader’s funds transfer request via phone or in person without worry.
Employees should be encouraged to resist the inclination to help and temper eagerness to prioritize requests from leadership.
The FBI considers BEC the most financially damaging scams in the U.S. Take action to ensure your company’s leadership and employees understand the threat of this scam, and how to identify BEC red flags and reduce risk.
Justin Rainey serves as chief information security officer and chief privacy officer at UMB Financial Corporation. In this role, he is responsible for establishing the strategy and implementation of an effective, integrated and proactive information security and privacy program. Connect with Justin at [email protected].